|
|
 |
|
|
 |
| |
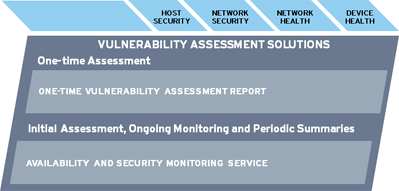 |
| |
 |
Business Benefits: |
| |
 |
Affordable
one-time cost |
 |
Objective,
independent perspective on your
organization's security exposure, for
communication to internal, external
stakeholders |
 |
Reduced
risk of legal liability from security
breaches or illegal use of corporate systems |
 |
Maintained trust from customers, suppliers, partners in
confidentiality of sensitive information and availability of
business-critical applications |
 |
Avoidance of
lost productivity, revenue loss from downtime
of business-critical applications or
compromised corporate data |
|
 |
IT Benefits: |
| |
 |
Data gathering
is largely automated, and non-intrusive,
with limited disruption to operations |
 |
Results are easy
to interpret in a management-friendly
"scorecard" format, with clear,
actionable, well-researched recommendations
|
 |
Employs a
combination of active and passive scanning
techniques
for the most comprehensive identification of
multiple types of security vulnerabilities |
 |
Assesses
vulnerabilities in people as well as
technology
using sophisticated password-cracking
techniques |
|
 |
Best Suited For: |
| |
 |
Companies needing an initial benchmark of their vulnerability
to technology and personnel-based "social engineering"
attacks |
 |
Organizations looking to complement or
refresh a prior security audit |
 |
Corporate security managers wanting to
validate adherence to security policies and
procedures |
|
 |
Technologies Employed: |
| |
|
|
|
 |
|
| |
|