|
|
 |
|
|
 |
| |
 |
| |
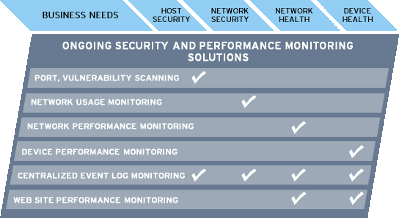
NetPersist's ongoing
security and performance monitoring services involve
connecting a hardened monitoring appliance
to your network, which continuously monitors your
computers and network devices for security and
performance vulnerabilities, and provides
easy-to-understand answers to everyday security,
performance, and Internet usage questions.
We are responsible
for performing ongoing monitoring and maintenance of
the system, and you access our reports on-demand via
a secure web-based interface.
The information we provide is designed specifically
to make it easy for you to identify security and
performance vulnerabilities before they become
outages or security breaches, but it is also
invaluable for rapidly pinpointing the problem if a
security incident or outage does occur.
|
 |
Business Benefits: |
| |
 |
Bandwidth cost
savings -
less wasted bandwidth can enable reductions
in bandwidth overage penalties or burstable
bandwidth limits, and lower monthly telecom
costs |
 |
Improved
employee productivity
through reduction in Internet mis-use and
downtime from outages or security incidents |
 |
Avoidance of
revenue loss, legal fees
or fines
from downtime of business-critical applications, compromised corporate
data, or non-compliance with Payment Card Industry (PCI) requirements |
 |
Superior
cost-effectiveness
compared to
purchasing, implementing, and maintaining
separate commercial products in-house |
|
 |
IT Benefits: |
| |
 |
Unprecedented
visibility into what is happening on
your network, and what devices or links are
vulnerable to compromise or are
under-performing/over-utilized |
 |
Ability
to rapidly detect and respond to
performance degradation or virus/worm
outbreaks if an incident does occur, and
monitor your network provider's Service
Level Agreement (SLA) compliance |
 |
Secure,
non-intrusive operation; service can
usually be up and running in 4 hours or less |
 |
Ability to
monitor a wide variety of platforms
including Microsoft, Linux, and Unix-based
computers and almost any network device,
in both
in-house and outsourced environments |
|
 |
Best Suited For: |
| |
 |
Companies with
limited or over-burdened I.T. resources
looking for an affordable, non-intrusive way
to facilitate troubleshooting and move
towards a regular program of proactive
maintenance |
 |
Companies with
dedicated I.T. security resources who
need a centralized, flexible, and
best-of-breed tool for collecting and
reporting security and performance
information |
 |
Corporate security managers wanting to
validate adherence to security policies and
procedures on an ongoing basis, rather
than relying on periodic security audits which
become out-of-date quickly |
 | Merchants required to provide proof of compliance with the Payment Card Industry Data Security Standard (PCI DSS) to their merchant bank / acquirer |
|
 |
Available Services: |
| |
 |
Periodic External Perimeter Assessment involving an external, in-depth 'hackers-eye view' scan of public IP addresses and a detailed review of perimeter device configuration and perimeter architecture relative to best-practices
|
 |
Periodic Password Assessment of Windows domain passwords using multiple commoly-used and freely-available password cracking techniques, providing a detailed report of which accounts were cracked and how, with specific, user-friendly recommendations on how to maximimze your employees' resistance to password attacks
|
 |
Periodic Executive Summaries including key cyber-security Performance Indicators, summaries of Mitigated/Oustanding/New cyber-security issues, and a Prioritized Remediation Plan based on all Assessment activities performed, presented in non-technical language |
 |
Periodic Port/Vulnerability scanning for missing patches, weak/default passwords, security misconfigurations on servers and workstations (considered a best-practice, and required for compliance with PCI-DSS, SOX, etc.)
|
 |
Real-time and Historical Network Usage
Profiling |
 |
High Risk
Traffic Pattern Detection / Alerting |
 |
Internet / VPN / WAN
Link
Performance Monitoring |
 |
Device
/ Server Performance Monitoring |
|
|
|
 |
|
| |
|