|
|
 |
|
|
 |
| |
 |
| |
 |
Business Benefits: |
| |
 |
Objective,
vendor-agnostic approach ensures the
solution we implement will be the best fit
with your specific requirements |
 |
Vendor
independence provides you with the
flexibility to purchase from your preferred
suppliers without being locked in |
 |
Reduced risk
of unexpected downtime or disruption
through an inclusive, structured methodology
and pre-staging/testing of solution in our
lab environment beforehand |
|
 |
IT Benefits: |
| |
 |
Inclusive,
flexible approach provides as much or
as little involvement in the design,
evaluation, and implementation as you
require |
 |
Thorough
documentation of the solution in a
"Configuration Run-Book" helps ensure that
it can be effectively maintained
post-implementation |
|
 |
Best Suited For: |
| |
 |
Companies
looking for specialized security design and
implementation expertise to perform
end-to-end project management and execution
of complex security technology projects
while transferring security skills and
knowledge to existing staff |
 |
Businesses
looking to augment existing staff for
security design or implementation efforts
they would like to manage internally |
|
 |
Available Services: |
| |
 |
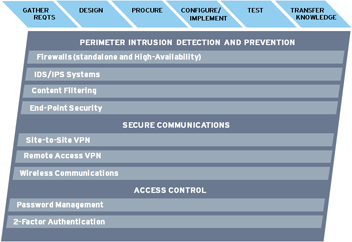
Assessment, inventory and
documentation of existing security infrastructure |
 |
Requirements Development and Design
of perimeter, VPN, or access-control
solutions |
 |
Competitive hardware
and/or software evaluation, selection and
procurement |
 |
Implementation, testing
and documentation of infrastructure |
 |
Training and knowledge
transfer to in-house staff, including lab
simulations |
|
|
|
 |
|
| |
|